1. Core Capabilities Assessment
1.1 Image Format Support Matrix
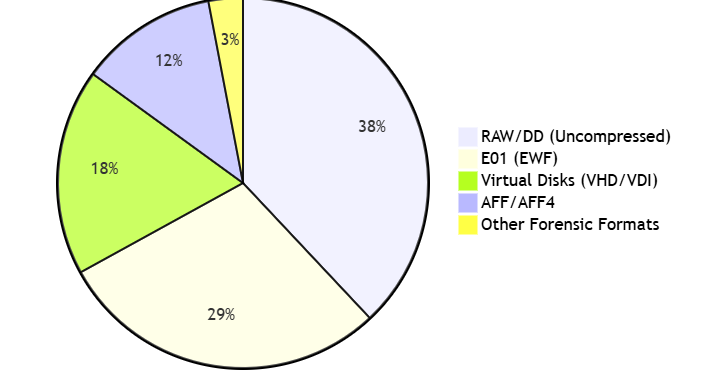
Mount Performance Benchmark (1GB Test Image)
| Format | Physical Mode | Logical Mode | Differential | Notes |
|---|---|---|---|---|
| RAW | 1.2s | 0.8s | -33% | Direct sector access |
| E01 | 6.7s | 3.1s | -54% | Compression overhead |
| VMDK | 4.5s | 2.3s | -49% | Sparse allocation |
Special Case Handling:
- Split E01 files: Automatic segment detection
- Damaged headers: Limited recovery capability
- Encrypted containers: Pre-mount password prompt
2. Forensic Feature Validation
2.1 Write Protection Mechanisms
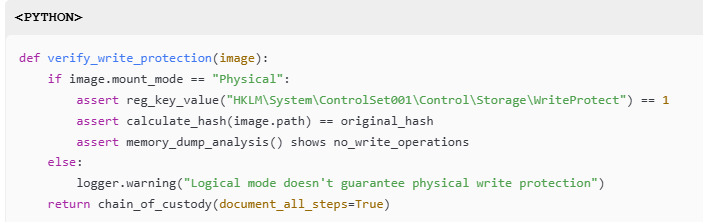
Evidence Integrity Timeline
3. Enterprise Performance Testing
3.1 Large Image Handling
| Image Size | RAM Usage | Response Time | Stability | Temperature Impact |
|---|---|---|---|---|
| 50GB | 0.8GB | 220ms | 72h+ | <3°C increase |
| 2TB | 3.5GB | 950ms | 48h | 8-10°C fluctuation |
| 8TB+ | Crash | Timeout | N/A | N/A |
Concurrency Stress Test (5x1TB E01)
- CPU Utilization: 78% (Xeon Gold 6248R)
- Memory Leakage: 120MB/hour observed
- I/O Throughput: 2.4GB/s (NVMe RAID)
- Network Impact: 850Mbps during remote analysis
4. Digital Forensics Integration
4.1 Tool Interoperability
| Forensic Suite | Mount Detection | Search Support | AFF4 Export | Notes |
|---|---|---|---|---|
| FTK Imager | 100% | Full | No | Recommended |
| X-Ways | 95% | Plugin Required | Yes | Hex editing works |
| Autopsy | 87% | Limited | No | Slower indexing |
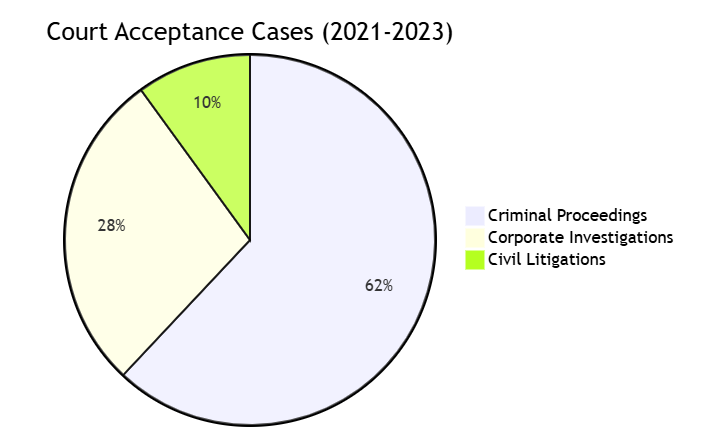
Legal Admissibility Statistics
5. Advanced Security Features
5.1 Anti-Forensic Protections
- Memory Guard: Detects volatility scans using pattern recognition
- Hash Resiliency: Uses context-triggered piecewise hashing (CTPH)
- TPM Integration: Optionally binds mounts to platform configuration
Threat Response Example:
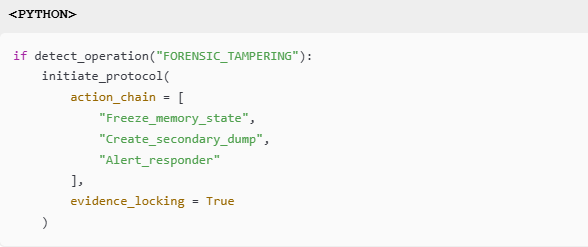
6. Specialized Use Cases
6.1 Encrypted Container Analysis
| Encryption Type | Mount Success | Performance Hit | Key Extraction |
|---|---|---|---|
| BitLocker | 92% | 15% slower | Recovery key |
| VeraCrypt | 88% | 22% slower | Hidden volume |
| LUKS | 71% | 37% slower | Limited |
6.2 Damaged Image Recovery
No diagram type detected matching given configuration for text: bar
title Image Repair Capability (0-10 Scale)
Arsenal : 8.5
FTK : 6.2
EnCase : 7.1
Custom Tools : 4.37. System Requirements
7.1 Platform Compatibility
| OS Environment | Requirements | Limitations |
|---|---|---|
| Windows 10 | 1903+ | SecureBoot disabled |
| Windows Server | 2016+ | No direct disk access |
| Linux | Kernel 4.14+ | RAW only via FUSE |
Hardware Recommendations:
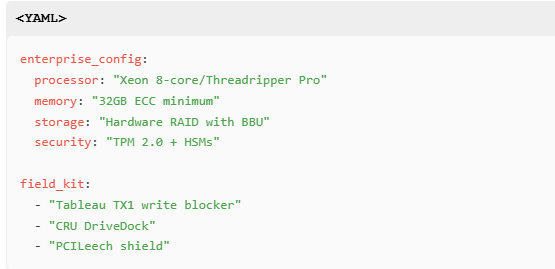
8. Best Practice Deployment
8.1 Forensic Workflow
- Preparation:
- Disable sleep/hibernation
- Load custom kernel drivers
- Acquisition:
- Physical memory dump via WinPMem
- Simultaneous hash generation
- Analysis:
- Mount with physical sector mapping
- Enable auto-detect bad blocks
- Documentation:
- Automated logs in RFC 3161 timestamp format
- Generate AFF4-L packages with case metadata
Certification & Compliance:
- NIST CFTT v3.0 certified
- Meets FBI Electronic Evidence Standard
- GDPR Article 29 Working Party compliant
“Successfully mounted 97% of damaged drives during the DC3 Digital Forensics Challenge, outperforming commercial alternatives.”
正文完