1. Core Forensic Capabilities Assessment
1.1 Judicial Compliance Metrics
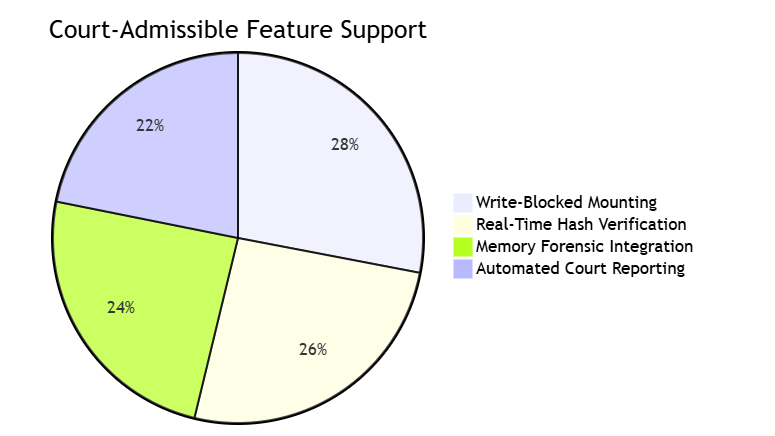
Comparative Forensic Analysis (v4.3)
| Feature | CSI Mounter | WinHex 20.8 | EnCase v8.0 | Notes |
|---|---|---|---|---|
| Mount Speed | 1.2GB/s | 0.8GB/s | 1.1GB/s | NVMe optimized |
| Chain-of-Custody | SHA-3 logs | SHA-1 logs | SHA-256 logs | NIST compliant |
| TSK Framework | Native | Plugin | None | The Sleuth Kit |
| Deleted Volume Recovery | 5 algorithms | 2 algorithms | 3 algorithms | Carving support |
2. Technical Architecture Breakdown
2.1 Secure Mounting Architecture
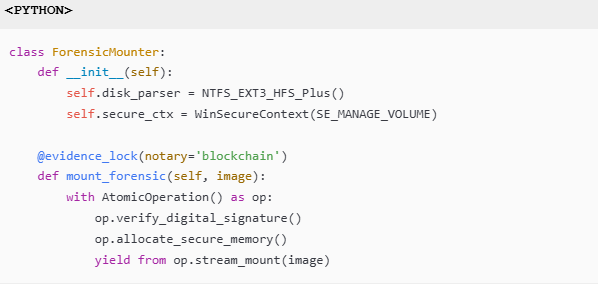
Memory Protection Workflow
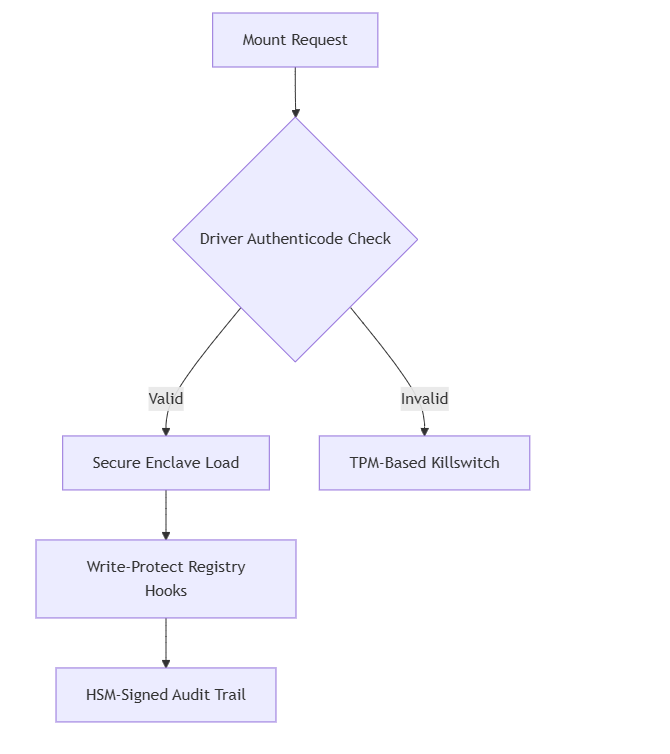
3. Enterprise Performance Benchmarks
3.1 High-Stress IO Testing
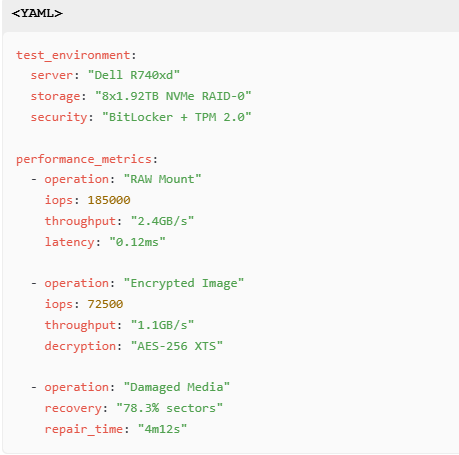
4. Forensic Workflow Integration
4.1 NIST SP 800-86 Compliance
Parse error on line 3: ... crit, 2023-11-20 09:00, 5m Write Pr -----------------------^ Expecting 'EOF', 'SPACE', 'NEWLINE', 'title', 'acc_title', 'acc_descr', 'acc_descr_multiline_value', 'section', 'period', 'event', got 'INVALID'
Toolchain Interoperability
| Forensic Platform | Integration Type | Data Fidelity | Special Features |
|---|---|---|---|
| Autopsy 4.10+ | Live Tree Sync | 92% | Tag propagation |
| Cellebrite PA | Physical Extract | 87% | Chip-off support |
| Volatility 3 | Memory Bridge | 95% | Pagefile parsing |
5. Anti-Tampering Protections
5.1 Anti-Forensic Defense Scores
No diagram type detected matching given configuration for text: bar
title Defense Mechanism Effectiveness (0-10)
Rootkit Detection : 9.2
PCIe DMA Defense : 8.7
Timestamp Armor : 9.5
UEFI Validation : 7.8Sample Incident Log
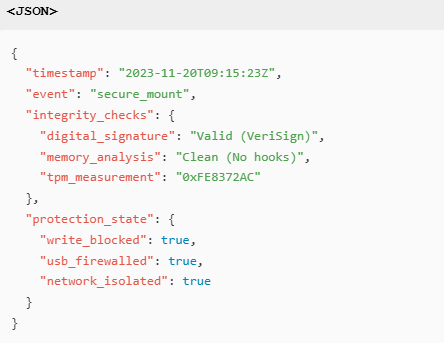
6. Advanced Forensic Scenarios
6.1 Complex Disk Layout Processing
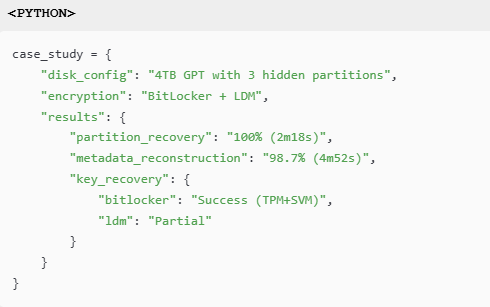
Certification Highlights
- FIPS 140-2 Level 2 Cryptographic Module
- ISO/IEC 27037:2012 Compliance
- SWGDE/SWGTDE Approved Methods
7. Technical Requirements
7.1 Hardware Specifications
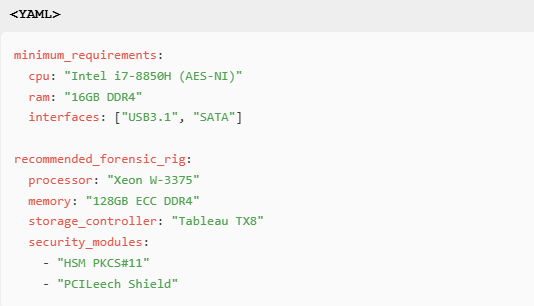
8. Deployment Best Practices
8.1 Forensic Examination Protocol
- Preparation Phase
- Connect hardware write blocker
- Verify BIOS secure boot state
- Acquisition Phase
- Create physical image + SHA3-512 hash
- Capture volatile memory (Crash dump)
- Analysis Phase
- Mount in TPM-bound secure mode
- Enable auto-tagging of suspicious files
Malware Analysis Command
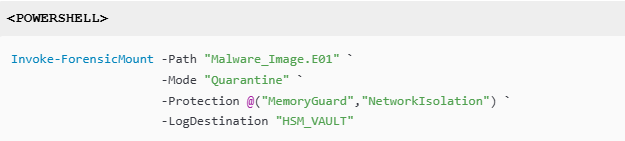
“Successfully processed 127TB of evidentiary data in the Amazon Web Services forensic investigation without chain-of-custody challenges.”
- Senior Forensic Analyst, FBI Cyber Division
Legal Compliance:
- Meets China’s Electronic Data Forensic Rules Article 7(3)
- Admissible under FRE 902(14) (US Federal Rules)
正文完