Having recently seen a number of requests on the security and forensic list servers that I participate in requesting recommendations / procedures for copying the disk (VMDK) for a specific Virtual Machine (VM) within a VMware environment for analysis in an incident response, I put together a quick How To in effort to provide some insight in to a few of the methods that I have used.
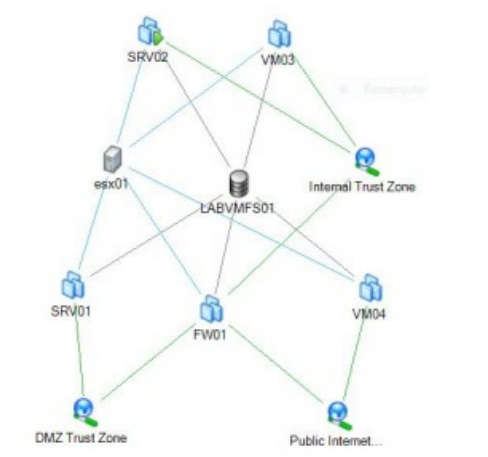
Most often the files associated with a given VM are not stored locally on the physical server running ESX or ESXi and the respective VM. It is important to understand that in order to use many of the more powerful features of VMware such as vMotion and DRS the files for the VM’s must reside on shared storage that is reachable from each ESX or ESXi server that needs to interact with it. Hence, when considering the acquisition of the files associated with a given VM you most often will not have the luxury of simply bringing down the physical server running ESX or ESXi and the respective VM and imaging the local hard drive as the files in question may not reside there. Further bringing down the server that is hosting the shared storage for the environment, removing the drives and using your hardware imager to copy the disk(s) will in all likelihood not be an option as there could be hundreds of other virtual machines sharing that same storage device for their files that simply cannot be taken down and must remain in production. As an example, in Figure 1 below we have 5 VM’s – SRV01, SRV02, VM03, VM04 and FW01 all using the shared storage on LABVMFS01. Taking down the shared storage LABVMFS01 for traditional drive imaging is not an option as it would also bring down the associated VM’s and they need to remain in production.