This blog post is a second edition and follow-up to Intro to Report Writing for Digital Forensics., which you’ve taken the time to review, digest, and dissect. How the digital forensic practitioner presents digital evidence to his/her intended audience (Regardless, of why we are preparing a digital forensic report), establishes proficiency of the digital forensic examination. Let’s take it even a step further, how will you present your findings? Effectively reporting what you found during your forensic examination will aid you in presenting your report and the digital evidence to whomever your intended audience will be, which ultimately may be a jury in a criminal or civil proceeding. In this blog post, we are going to tackle some more report writing issues. Remember, YMMV depending on what hat you wear in digital forensics and who you will be reporting the findings to from your digital forensic examination. So how can you be effective at completing your forensic report and presenting your findings? Depending on where you fall as a digital forensic examiner/analyst, you have to win in the field to win in the courtroom! This is your time as the examiner/analyst (Maybe expert witness?) to tell a story (Are you creating a timeline or super-timeline during your forensic analysis?) of the digital evidence or even lack thereof and how it relates to the details of the case. This is your time to shine and communicate your work product to your audience! Stick to the facts and be straight-forward with the evidence.
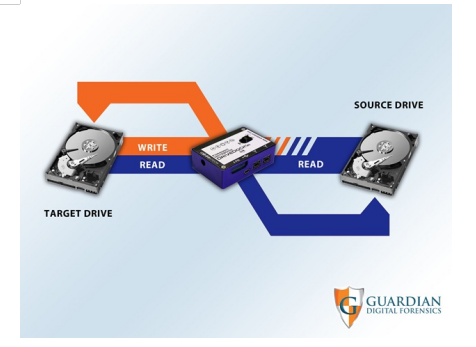
If you fail to effectively report your findings, your analysis will quickly be forgotten as your reader is left to draw their own conclusion or worse, turn elsewhere for the answer. Your forensic report should be a balance of technical detail, presented in a simplistic fashion, and tailored for your audience. Avoid link dumping or, “I used ABC automated forensics tool, exported SAM registry hive, exported all e-mail & pictures, and burned the report to a CD”. How much of that data is relevant to the case? Recently, Benjamin Wright, Esq. wrote a great article titled, “Investigators: How To Write A Report and Store Digital Evidence”. Benjamin states, “As an educational exercise, I have developed a prototype, online investigation report and evidence container. Part check-list, part demonstration, this prototype could be useful for many kinds of non-criminal investigations. Using the Zoho online notebook application, I created the prototype as a teaching tool for my SANS course on the law of investigations.” Take some time to read his blog article and take a look at the Zoho online notebook if you haven’t. As Benjamin points out this could be a useful tool in non-criminal investigations.
When you are preparing your report your first section as I discussed in Part I, will be an “Overview/Case Summary”. In this section, remember you are defining your role handling the digital evidence and why a forensic examination is being conducted. This is an abstract/synopsis of your forensic examination and straight-forward.You will include the technical details in the “Findings and Report (Forensic Analysis)”. In some cases, a case summary may be sufficient for what your client/prosecutor/attorney is requesting. It is also good to keep a detailed forensic report for your records (per your department/company policy) in anticipation of legal proceedings. Your case summary should be written to the level where the non-technical reader will grasp and understand your findings. Lars Daniel with Guardian Digital Forensics blogged about presenting technical data to a non-technical audience here and here. Corey Harrell has a good blog post here on the Digital Forensic Investigation process. I mention this because you have to know where you are to get where you are going with your investigation and reporting is an integral part of this process.