Structured Reporting Framework
- Executive Briefing
- Prioritizes business impact over technical details
- Case Study: Identified game credential-stealing malware on a corporate file server through:
- Process injection patterns
- Memory scraping techniques
- Contextual South Korean gaming references [2]
- Operational Response Section
- Critical IOCs presented in actionable formats:<MARKDOWN>
## File Indicators- Variant naming patterns (20+ observed)- Hash values (SHA-256 preferred)## System Artifacts - Persistent registry keys - Service installation paths - Includes relevant patch KB numbers for exploited vulnerabilities [2]
- Critical IOCs presented in actionable formats:<MARKDOWN>
- Technical Appendix
- Preserves detailed reversing methodology
- References open-source tools like Ghidra alongside commercial options
Modern IOC Deployment Strategies
Network Hunting Techniques
- Automated Triage
- YARA rule deployment via Kestrel threat hunting language
- OpenIOC-based scanning with modern EDR platforms
- Progressive Analysis
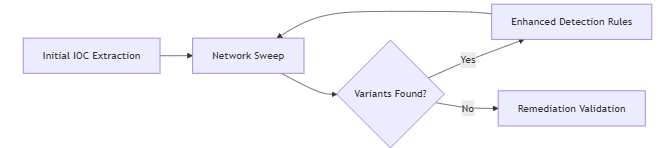
- Cloud-Scale Analysis
- Utilize Sigma rules for log-based detection
- Implement unsupervised learning for anomaly detection [2]
Resource Optimization Guidance
For Time-Constrained Teams:
- Focus on critical business systems first
- Implement automated IOC validation checks
For Comprehensive Response:
- Deploy iterative hunting cycles
- Establish baselines using MITRE ATT&CK techniques
- Leverage threat intelligence platforms for expanded detection
“Effective reporting bridges the gap between technical findings and organizational risk decisions.” — Incident Response Principle
Upcoming in this series: Comparative analysis of static/dynamic/hybrid malware analysis approaches for different response scenarios.
正文完