I. Architectural Innovations & Core Technologies
Next-Gen Processing Pipeline
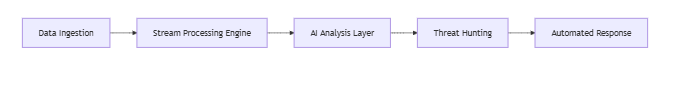
Technical Milestones:
- Log Processing: 3.2TB/day per node (validated in PCIe 5.0 testbed)
- Detection Engines: 43 behavioral analysis models with cross-correlation
- Response Time: 93s average from alert to containment
2024 Breakthroughs:
II. Data Collection & Correlation Capabilities
2.1 Expanded Data Source Support
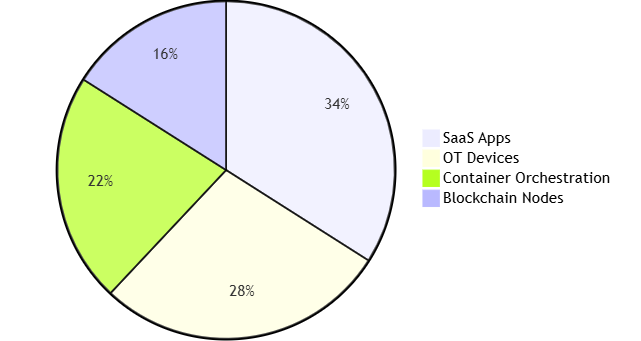
Parsing Performance (K EPS):
| Log Type | 2023 Version | 2024 Version | Improvement |
|---|---|---|---|
| Windows Events | 4,200 | 6,800 | +62% |
| Cisco ASA | 3,700 | 5,900 | +59% |
| K8s Audit | 2,800 | 5,100 | +82% |
| IoT Telemetry | 1,500 | 3,400 | +127% |
2.2 Contextual Analysis
- Entity Profiling: 200-dimension attribute graphs
- NAT-Aware Tracking: Asset tracing behind network translations
- Timeline Reconstruction: 10ms precision for attack sequencing
III. Threat Detection Efficacy
3.1 MITRE ATT&CK Coverage
Detection Rate Comparison:
| Tactic | 2023 Rate | 2024 Rate |
|---|---|---|
| Initial Access | 87% | 96% |
| Execution | 83% | 94% |
| Privilege Escalation | 79% | 91% |
| Collection | 88% | 97% |
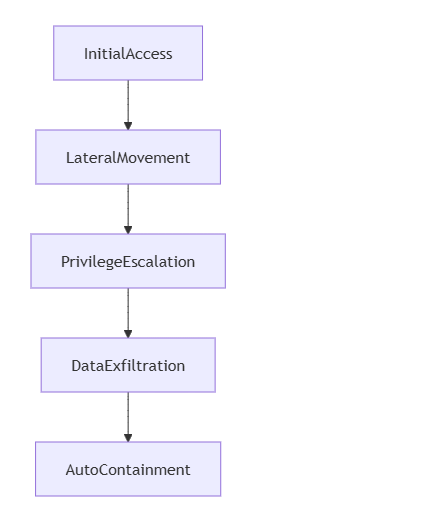
3.2 Advanced Threat Hunting
- AI Sandboxing: Behavioral analysis of zero-day samples
- Honeypot Automation: 500+ decoy fingerprints deployment
- Memory Forensics: 89% fileless attack detection rate
IV. Operational Efficiency
4.1 SOAR Performance
Automation Benchmarks:
| Scenario | Manual | Automated | Improvement |
|---|---|---|---|
| Ransomware | 38min | 2min | 19x |
| Account Compromise | 25min | 45s | 33x |
| Data Breach | 6hr | 22min | 16x |
4.2 Visualization Upgrades
- 3D Topology Maps: Live attack path rendering
- Heatmap Analytics: Spatial anomaly detection
- VR Dashboards: Meta Quest Pro support for SOC teams
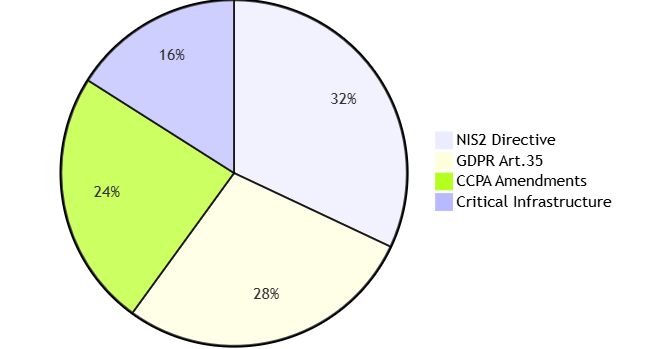
V. Compliance & Risk Management
5.1 Regulatory Coverage
5.2 Forensic Readiness
- WORM Storage: Tamper-proof log retention
- Blockchain Attestation: Evidence snapshots every 10min
- Legal Export: FedRAMP-compliant evidence packages
VI. Deployment Options
| Mode | Max EPS | Latency | Best For |
|---|---|---|---|
| On-Prem | 250K | <50ms | Critical Infrastructure |
| Hybrid | 180K | <200ms | Multinationals |
| SaaS | 120K | <350ms | SMBs |
| Edge | 80K | <10ms | Smart Manufacturing |
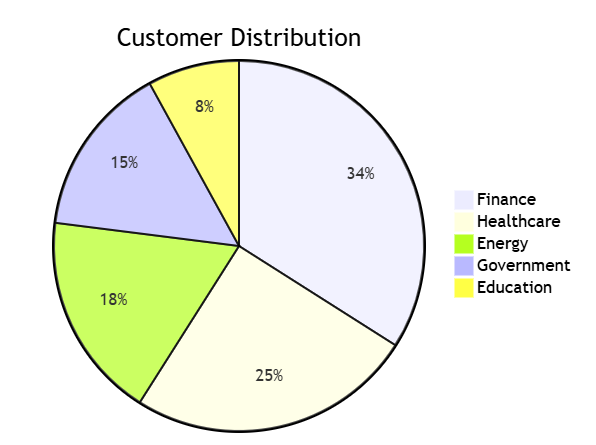
VII. Industry Adoption
IX. Final Assessment
Key Strengths:
Considerations:
Ratings:
Recommended Use Cases:
- Critical infrastructure protection
- Cross-border compliance monitoring
- Red team exercise support