It’s been a while since I’ve written about this topic, and in that time, there have been some useful security updates provided by Microsoft, as well as some troubling developments with Microsoft’s Kerberos implementation. In order to fully cover these topics, I’m going to split the discussion into two articles. This article will cover specific updates Microsoft has provided to help protect user credentials. I’ll follow up next week to discuss the Kerberos issues in depth.
As a quick reminder, the major takeaway from my previous articles on this subject are that we can successfully protect our privileged domain accounts by taking these 3 steps:
Let’s take a look at the changes in the newest Microsoft operating systems, as well as recent patches for older operating systems, that have helped with each of these 3 areas.
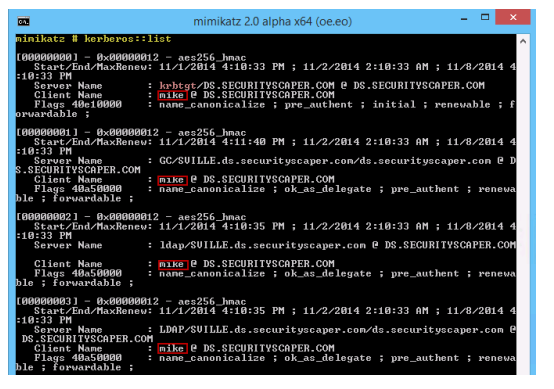
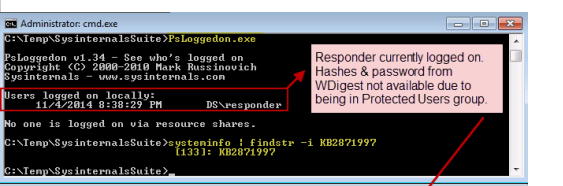
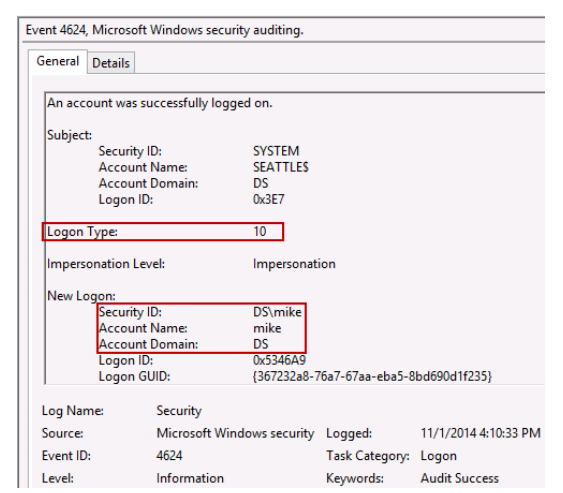
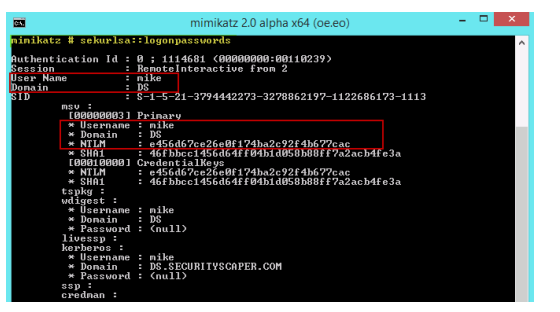
Of the 3 steps we should take to protect our privileged domain accounts, avoiding interactive logons is the most important because traditional interactive logons store the keys to a user’s kingdom?including password hashes, Kerberos keys and tickets, and even the password itself. I used the word “traditional” because we now have a new type of interactive logon that mitigates this credential exposure, called Restricted Admin Remote Desktop. More on that in a moment.
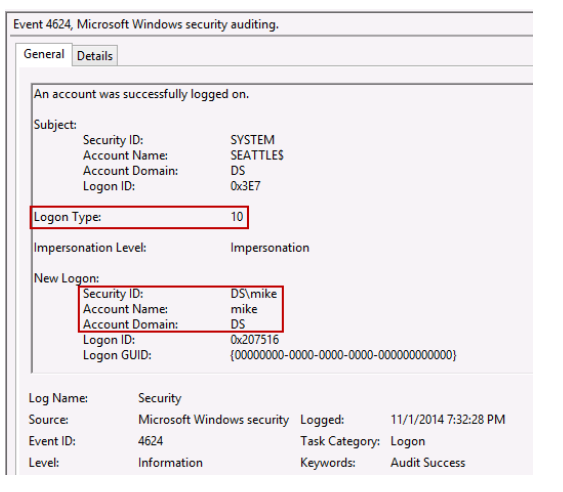
The previous password hashes article in this series includes a detailed look at what constitutes an interactive logon, but to quickly summarize, it includes the following: local desktop logons at the console, remote desktop logons via RDP/VNC/Citrix and the like, and even RunAs logons. Although less common, an interactive logon can also be generated programmatically with tools such as PsExec when the “-u” option is invoked.
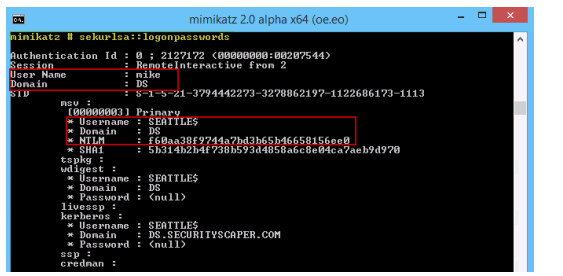
So rather than logging on interactively, exposing all of those credentials, you should instead connect with network logons remotely using tools such as PowerShell Remoting, WMI/WMIC, as well as most SMB/CIFS connections such as mapping drives, using Computer Management, etc.
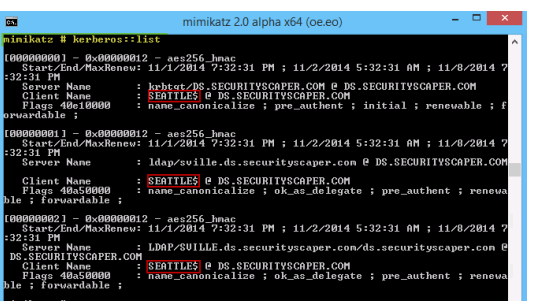
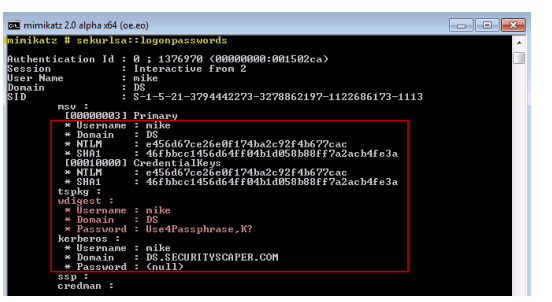
That said, a feature in Windows 8.1 and Server 2012R2 provides a modified version of an interactive logon which has the same beneficial effect of a network logon?it does not store the user’s credentials on the remote system.
Here’s a look at the description of this feature from the new Remote Desktop client’s help dialog box (run “mstsc /?” from a command prompt):