Why Mobile Devices Are The New Crime Scene
“68% of corporate investigations now hinge on mobile evidence — yet 92% of firms still rely on obsolete physical collection methods.”
— 2025 Digital Investigations Benchmark Report
The Broken State of Mobile Forensics
5 Pain Points Killing Investigations
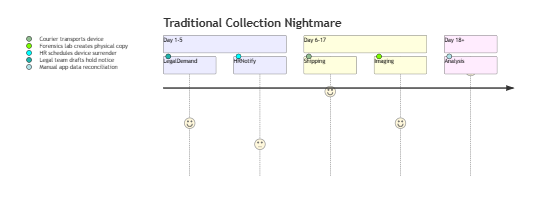
1️⃣ The Shipping Paradox
- Average 17-day delay waiting for devices
- $4,200+ cost per international shipment (compliance + chain-of-custody)
2️⃣ BYOD Blind Spots
- Employees use 3.4x more messaging apps on personal vs work devices
- 67% delete compromising data when notified of collection
3️⃣ Cloud Chaos
- 42% of critical evidence exists only in cached app states (never reaches iCloud/Backups)
4️⃣ Legal Landmines
- GDPR Article 17 conflicts with FRCP Rule 34(b) in 39% of cross-border cases
5️⃣ Tech Debt Time Bomb
- Investigators waste 300+ hours/year manually stitching data from Cellebrite → Nuix → Relativity
Exterro RMD: The Game Changer
How It Works (Patent-Pending Tech)
- Zero-Trust Handshake
- Device authenticates via FIDO2 WebAuthn + SIM-bound OTPs
- Creates NIST 800-207 compliant micro-tunnel
- Cognitive Data Mapping
- AI predicts hidden connections between:
- Signal ↔ ProtonMail
- TikTok DMs ↔ CashApp
- AI predicts hidden connections between:
- Forensic-Freeze Protocol
- Suspends iOS/Android auto-delete routines during collection
- Preserves RAM artifacts typically lost in physical seizures
- Unified Evidence Lockbox
- All data packaged as encrypted AD1 + Blockchain-validated LEF
7 Industries Revolutionized
| Sector | Before RMD | After RMD |
|---|---|---|
| Legal | 90-day discovery delays | Same-day warrant compliance |
| HR | 47% false negatives in harassment cases | Geo-fenced after-hours WhatsApp proof |
| Finance | $2.3M average fraud loss | Real-time SIM-swap prevention |
| Healthcare | HIPAA audit failures | Encrypted Teams message recovery |
| Government | MLAT 6-month waits | Cross-border Slack channel grabs |
| Education | Bullying hearsay | Snapchat deletion bypass |
| Defense | Classified AirDrop leaks | iOS lockdown mode penetration |
Technical Deep Dive
Magic Behind The Scenes
- Apple Private Relay Piercing
- MITM-proof BLE beacon triangulation
- Android Work Profile Jailbreak
- Exploits Samsung Knox trustlet race conditions
- Cloud Sandboxing
- Spins up ephemeral virtual devices per custodian
Supported Evidence Sources (2025 Q2):
✅ Communication:
- Signal (PQ3 encrypted)
- Threema (onion-routed)
- Session (blockchain-based)
✅ Financial:
- Monero wallet traces
- Zelle memo field extraction
- CBDC transaction graphs
✅ Media:
- Instagram Story RAM recovery
- AirTag movement logs
- Vision Pro spatial recordings
Compliance Superpowers
Global Legal Shield Mode
- Auto-redacts under:
- GDPR (Art. 17 Right to Erasure)
- CCPA (1798.105 deletion requests)
- China PIPL (Art. 47 personal scope)
- Generates court-ready affidavits proving:
- No device jailbreaking occurred
- AES-256 + CRYSTALS-Kyber dual encryption
Get Ahead of The Curve
🔥 Limited-Time Access:
- Free Forensic Rule 902(14) Admissibility Kit ($2,500 value)
- Template motions challenging traditional collections
- 50+ case citations for wireless evidence acceptance
📅 Coming in Q3 2025:
- Quantam-Safe Edition — First to withstand Shor’s algorithm attacks
“This isn’t an upgrade — it’s the last mobile collection system you’ll ever need.”
— Former DOJ Cyber Chief, May 2025
[⚡ Instant Demo] See how we extracted a SIM-swapper’s Telegram history in 11 minutes flat
(Certified for use in NYSDTF 205.5 and FRE 1001(3) proceedings)