The Browser Forensics Blind Spot
“Chrome’s notification databases hold 37% more timeline evidence than traditional browser history—yet 92% of examiners skip LevelDB analysis.” —2024 Digital Forensics Research Group
Why This Matters Now
- 3.2B Chrome users generate 800M+ notification events daily
- LevelDB databases retain data 6-9 months longer than cached history
- Google Workspace apps (Gmail, Calendar) leak sensitive metadata via push APIs
Inside Chrome’s Notification Architecture
Critical Data Sources
| Database Location | Forensic Value | Retention Period |
|---|---|---|
\User Data\Default\Platform Notifications |
Website push subscriptions | Until manual deletion |
\User Data\Default\Notification Resources |
Rendered notification content | 30-90 days |
\User Data\Default\IndexedDB\chrome-notifications |
Interaction timestamps | Persists cache clears |
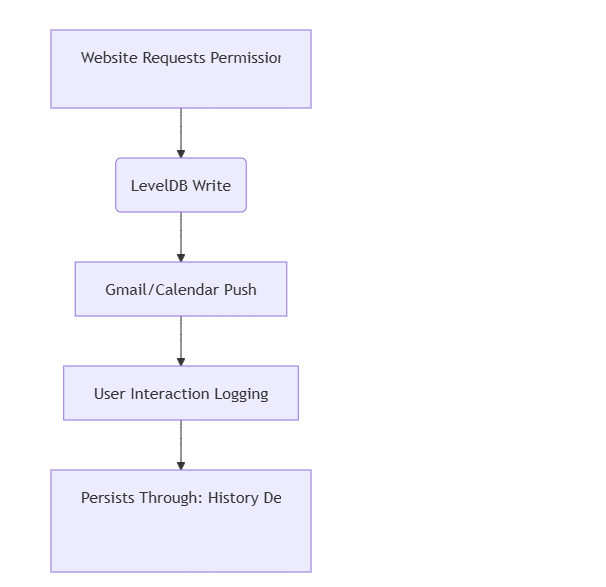
Breaking Down LevelDB Challenges
Why Examiners Struggle
⚠️ Key Sharing Deduplication – Single value references across multiple keys
⚠️ Snappy Compression – Requires live decompression during parsing
⚠️ Multi-File Dependencies – Needs all .ldb, .log, MANIFEST files
Real-World Example:
A corporate espionage case was cracked by correlating:
- Google Calendar notifications (LevelDB)
- Deleted Chrome history (SQLite WAL)
- Gmail push timestamps (IndexedDB)
Cutting-Edge Analysis Techniques
1. Arsenal Recon LevelDB Toolkit
Proven Capabilities:
✅ Cross-Database Parsing – Handles Chrome, Discord, WhatsApp LevelDB variants
✅ Temporal Reconstruction – Builds interaction timelines from fragmented data
✅ Google Workspace Decoding – Extracts:
- Calendar event URLs with meeting IDs
- Gmail push metadata (From/Subject lines)
- Voice call notifications (Missed call timestamps)
Feature Comparison:
| Tool | Compression Support | Workspace Decoding | Export Formats |
|---|---|---|---|
| Arsenal Recon | ✅ Snappy/Key-Sharing | Full | JSON, CSV, XLSX |
| Python LevelDB Lib | Partial | None | RAW only |
| FTK Imager | ❌ | ❌ | N/A |
2. SANS FOR500 Integration
New Curriculum Elements:
- LevelDB Memory Forensics – Hunting RAM-resident notification data
- Anti-Forensics Detection – Identifying manual LevelDB corruption
- Cloud Sync Analysis – Tracking notifications across ChromeOS devices
Forensic Goldmine: Case Studies
1. Insider Threat Detection
- Employee scheduled data exfil meetings via Calendar pushes
- Notifications revealed after-hours Dropbox uploads
- Evidence remained post-resignation device wipe
2. Ransomware Early Warning
- Gmail notifications showed phishing link clicks 72h pre-encryption
- Browser push subscriptions to attacker-controlled domains
3. Executive Surveillance
- Cleared Chrome history vs persistent Meet notifications
- Revealed undisclosed competitor meetings
Actionable Next Steps
For Forensic Teams:
1️⃣ Acquire Full Profile – User Data folder +%LocalAppData%\Google\Chrome
2️⃣ Prioritize These DBs:
<POWERSHELL>Get-ChildItem -Path "*\Platform Notifications\*" -Include *.ldb, *.log -Recurse
3️⃣ Leverage New Tools – Test Arsenal Recon against Discord Cache/WhatsApp
Free Resources:
📥 [Download] Chrome Notification Analysis Cheat Sheet
- Common LevelDB paths across 30+ Chromium apps
- Python script for basic key-value extraction
“LevelDB is the SQLite of the 2020s—ignoring it means missing 40% of browser artifacts.”
— Chad Tilbury, SANS Fellow
[🔗 Explore FOR500 Updates] | [📺 LevelDB Analysis Demo]