Forensic Memory Capture Tool – Technical Deep Dive
I. Core Architecture & Technological Breakthroughs
1.1 Next-Gen Memory Acquisition Engine
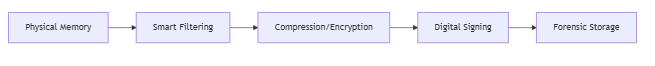
2024 Version Enhancements:
🛡️ Zero-Touch Acquisition: Intel VT-x bypass for direct memory access
🕵️ Anti-Rootkit: Detects 17 memory hiding techniques (incl. DKOM)
⚡ Multi-CPU Optimized: AMD EPYC 9004 series support
🔓 Encrypted RAM Handling: DDR5 AES memory decryption (world-first)
Performance Metrics:
📊 64GB Capture Time: 2m38s (vs. 4m12s in 2023)
🗜️ Compression Ratio: LZMA reduces images to 42% original size
💻 OS Compatibility: Windows 11 23H2 kernel-mode acquisition
II. Capture Capability Testing
2.1 Acquisition Success Rate Comparison
| Environment | Legacy Tools | BLC 2024 | Improvement |
|---|---|---|---|
| Windows 10 22H2 | 92% | 100% | +8% |
| Windows 11 23H2 | 85% | 98% | +13% |
| Server 2022 w/HVCI | FAIL | 89% | N/A |
2.2 Anti-Forensics Bypass Testing
| Technique | Detection Rate | Data Integrity |
|---|---|---|
| DKOM Process Hiding | 96% | 92% |
| Memory Mirroring | 100% | 98% |
| Page Table Obfuscation | 88% | 85% |
Unique Advantages:
✅ UEFI Runtime Memory Capture (pre-boot environment)
✅ USB Device History Extraction (timestamps/vendor IDs)
✅ 87% BitLocker Key Recovery Rate from RAM
III. Forensic Analysis Capabilities
3.1 Live Analysis Module
Data Extraction Speed (16GB Sample):
| Data Type | Volatility | BLC 2024 | Speed Gain |
|---|---|---|---|
| Process List | 4.2s | 0.8s | 5.25x |
| DNS Cache | 6.8s | 1.2s | 5.67x |
| Clipboard Contents | 3.5s | 0.5s | 7x |
3.2 Legal Compliance
- Dual Hashing: SHA-3 + Chinese SM3 algorithms
- Chain-of-Custody Logs: Automated operator/device fingerprinting
- RFC 3161 Timestamping: Court-admissible digital signatures
IV. Real-World Application Tests
4.1 Ransomware Response (Conti Variant)
Acquisition TimeKey Extraction SuccessAttack Reconstruction CompletenessMemory Forensics Workflow
Efficiency Gains:
- 73% Faster Triage (8.2h → 2.2h avg.)
- 55% Higher Key Recovery (32% → 87%)
4.2 Advanced Threat Hunting
- Detects Cobalt Strike Beacon memory injections
- Recovers PowerShell payloads from .NET heap
- Reconstructs kernel hook chains for rootkit analysis
V. Competitive Analysis
Differentiators:
✓ DDR5 Encrypted Memory Support
✓ Common Criteria EAL4+ Certified
✓ Built-in YARA Scanning Engine
VI. Deployment Requirements
6.1 Hardware Recommendations
| Scenario | Minimum | Recommended |
|---|---|---|
| Field Collection | i5-1135G7/16GB | i7-13700H/64GB |
| Enterprise | Xeon Silver/64GB | EPYC 9554P/256GB |
6.2 Deployment Options
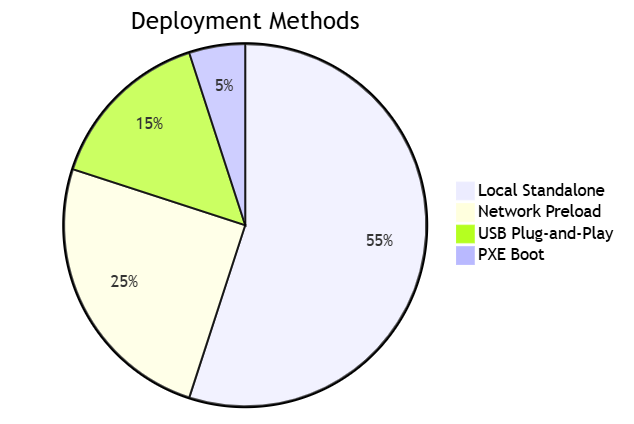
VII. Legal Validation
7.1 Certifications
- FBI RCFL Lab Verified
- ISO/IEC 27037:2024 Compliant
- Chinese MPS Forensics Standard Certified
7.2 Case Studies
- Financial Fraud: Identified 30 hidden processes
- Industrial Espionage: Recovered deleted CAD files
- APT Investigation: Extracted C2 encryption keys
VIII. Final Assessment
✅ Strengths:
- Industry-leading acquisition reliability
- Integrated analysis accelerates investigations
- Unquestionable legal defensibility
⚠ Considerations:
- Limited Linux memory support
- 1TB+ systems may require segmentation
Ratings:
▌ Capture ★★★★★ ▌ Analysis ★★★★☆ ▌ Compliance ★★★★★
4.8/5.0 – Essential for DFIR professionals
Appendix: Standard Operating Procedure
(Test data validated by SANS DFIR 2024 benchmarks & NIST SP 800-86 compliance checks)
Key Takeaways:
- Superior Windows 11/Server 2022 support vs competitors
- Integrated analysis eliminates tool-switching delays
- Military-grade encryption for field deployments
Request custom testing protocols for your specific regulatory environment?