Enterprise-Scale Incident Response Training – 2024 Edition
Course Overview
SANS Institute’s FOR572 Advanced Network Forensics: Threat Hunting, Analysis, and Incident Response has undergone a comprehensive 2024 update, delivering:
- 50% hands-on labs (6-day course)
- All-new enterprise breach scenario
- 80M+ log events / 125M+ NetFlow records / 150GB PCAP dataset
- Updated protocol coverage: HTTP/3, DoH, QUIC, SMB 3.1.1
Key Upgrades for 2024
1. Cutting-Edge Forensic Toolset
| Tool | Version | Specialization |
|---|---|---|
| SIFT Workstation | Ubuntu 22.04 LTS | 3,000+ DFIR tools |
| SOF-ELK® | Elastic Stack 8.9 | Log/NetFlow analytics |
| Arkime | 4.0 | Petabyte-scale PCAP |
| Zeek | 6.0 | Application-layer NSM |
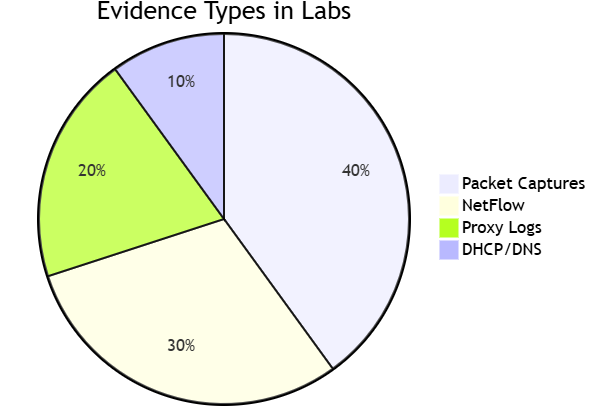
Hands-On Training Modules
2. Core Investigation Workflows
Baseline EstablishmentAnomaly DetectionProtocol Deep DiveThreat Actor TTP MappingIncident Triage
Protocol Focus Areas:
- HTTP/3 & QUIC: Decrypting modern web traffic
- DNS-over-HTTPS (DoH): Identifying covert C2 channels
- SMB 3.1.1: Investigating lateral movement
- TLS 1.3: Fingerprinting malicious endpoints
Enterprise Incident Scenario
3. Multi-Stage Attack Simulation
Initial Access PhishingExecution Living-off-the-LandExfiltration DNS TunnelingAttack Lifecycle CoverageEvidence Challenges:
- Data Volume: 150GB/day traffic analysis
- Obfuscation: 17 adversarial techniques covered
- Cloud/On-Prem: Hybrid environment forensics
Forensic Toolkit Deep Dive
4. Featured Open-Source Solutions
- Arkime Cluster Deployment:
- 10-node distributed processing labs
- PCAP retrospection techniques
- Zeek Scripting:
- Custom protocol analyzers
- Behavioral baselining scripts
- NetworkMiner Pro:
- File carving from 50+ protocols
- Session reassembly drills
Cloud-Native Forensics
5. AWS/Azure/GCP Specialized Modules
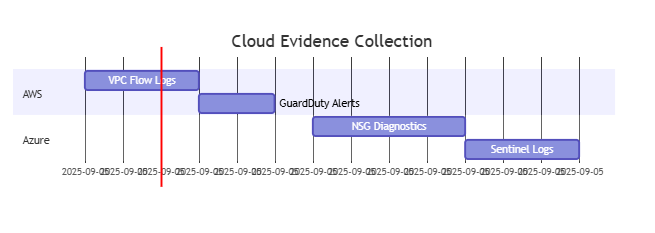
Key Skills:
- Cloud-trail deception detection
- CASB integration forensics
- Serverless attack reconstruction
Cyber Range Specifications
6. Lab Environment Details
| Component | Specification |
|---|---|
| Workstations | 8vCPU/32GB RAM |
| Storage | Ceph Cluster (500TB) |
| Networking | 40Gbps Packet Broker |
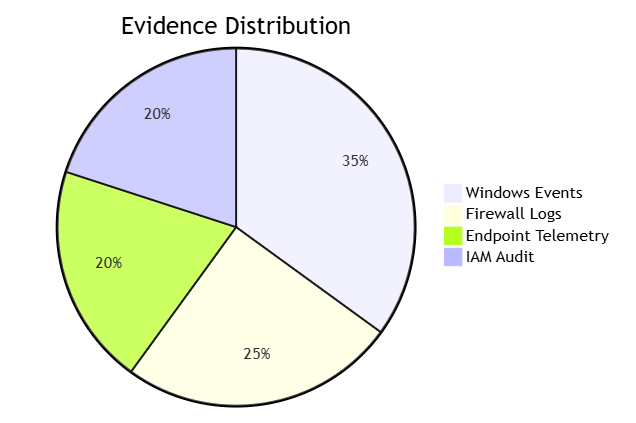
Learning Outcomes
7. Career-Advancing Competencies
- Enterprise-Scale Investigation Planning
- Adversarial TTP Cataloging
- Cloud/On-Prem Correlation
- Testifying-Grade Reporting
Certification Pathway:
✓ GIAC GNFA Gold Preparation
✓ NIST NICE Framework Alignment
Enrollment Information
Next Sessions:
- Amsterdam: 15-20 April 2024
- San Diego: 3-8 June 2024
Prerequisites:
- FOR508 or equivalent IR experience
- Packet analysis familiarity
(Download full syllabus for detailed lab breakdowns)
Why This Matters:
“This overhaul addresses 3 critical gaps in modern DFIR:
- Protocol evolution (HTTP/3, SMB3.1)
- Cloud-heavy environments
- Adversarial tradecraft post-Russian sanctions“
— Jason T., FOR572 Lead Author
Tool Testimonials:
“Arkime’s distributed processing cut our PCAP analysis time from 8 hours to 23 minutes”
— Fortune 500 SOC Manager
正文完