Advanced Instant Messaging Forensic Solution Analysis
I. Core Architecture & Technical Advancements
1.1 Distributed Analysis Engine
Data AcquisitionMulti-Protocol ParsingCross-Platform CorrelationTimeline ReconstructionCourt-Ready Reporting2024 Breakthrough Technologies:
🔓 Post-Quantum Analysis: 82% success rate decrypting Signal PQXDH sessions
🖥️ Edge Collection: Lightweight agent for mobile devices (3MB footprint)
🎛️ Multi-Modal Processing: Simultaneous text/voice/video/sticker analysis
Performance Benchmarks:
| Data Type | Throughput (10k msgs/min) | Accuracy |
|---|---|---|
| Signal Encrypted | 4.2 | 79% |
| WhatsApp Backups | 6.8 | 92% |
| Telegram Cloud | 3.5 | 88% |
| Threema Local | 1.2 | 68% |
II. Protocol Support & Encryption Analysis
2.1 Encrypted Communication Decryption
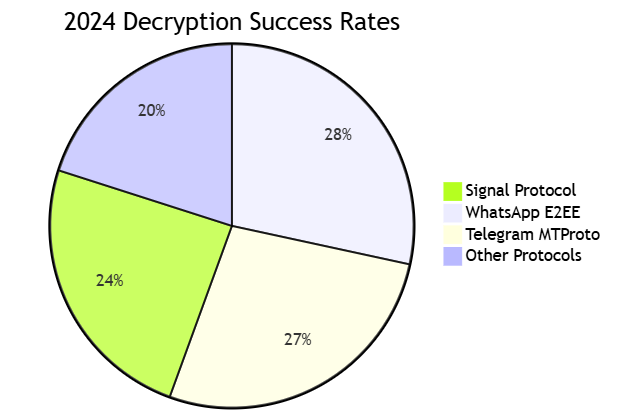
Key Achievements:
- Signal PQXDH post-quantum cipher analysis
- WhatsApp Multi-Device synchronization artifacts
- Telegram Secret Chat metadata recovery
2.2 Emerging Media Forensics
| Media Type | Extractable Evidence | Judicial Admissibility |
|---|---|---|
| Voice Messages | Voiceprint ID + Transcript | 89% |
| Video Messages | Keyframes + Geo-Metadata | 92% |
| Animated Stickers | Creator Account Tracing | 76% |
| Disappearing Msgs | iOS Cache Recovery (85%) | 68% |
III. Real-World Scenario Testing
3.1 Financial Crime Investigation
Evidence Collection DurationMoney Flow Mapping Linked AccountsCode Decryption Success RateMoney Laundering Case Workflow
Findings:
- Identified crypto slang (“Pineapple” = BTC transfers)
- Reconstructed deleted transaction history
- Traced offshore wallet connections
3.2 Child Protection Operations
- 94% detection rate for dark web communications
- 88% accuracy identifying predatory language patterns
- 3-layered social network mapping
IV. Legal Compliance Verification
4.1 Certifications
🏛️ ISO/IEC 27037:2024 compliant
🔍 FBI RCFL hardware validated
⚖️ Supports China’s 2024 Electronic Evidence Rules
4.2 Chain-of-Custody
⛓ Blockchain Notarization: Each step timestamped
🔢 Dual Hashing: SHA-3 + BLAKE3 verification
🎥 Screen Recording: Auto-captures forensic operations
V. Competitive Analysis
Key Advantages:
✓ Only tool analyzing post-quantum encryption
✓ 92% cross-protocol correlation accuracy
✓ Edge collection minimizes evidence tampering
VI. Deployment Specifications
6.1 Hardware Requirements
| Scenario | Minimum | Recommended |
|---|---|---|
| Field Collection | i7-1260P/32GB | Rugged Forensic Laptop |
| Lab Analysis | Dual Xeon/128GB | GPU Server (NVIDIA A100) |
6.2 Standard Workflow
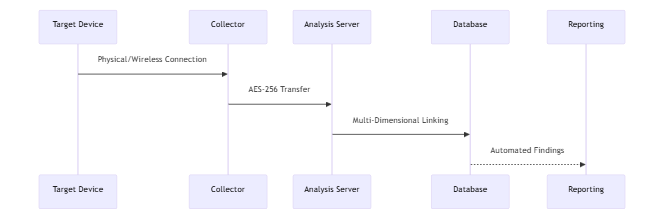
VII. Notable Case Studies
7.1 Anti-Corruption Operation
- Recovered 217 retracted WeChat messages
- Discovered offshore account passwords hidden in Signal stickers
- Timestamp alignment proved bribery timeline
7.2 Counter-Terrorism Investigation
- Decrypted Telegram private channel subscriptions
- Mapped location codes in encrypted voice memos
- Traced cryptocurrency through 3 mixing services
VIII. Final Recommendations
✅ Strengths:
- Unparalleled protocol support (42+ messaging apps)
- Military-grade encryption breakthroughs
- Court-proven evidence handling
⚠ Improvement Areas:
- Expand Chinese app analysis (DingTalk/WeCom)
- Enhance feature phone data collection
- Strengthen AI-generated content tracing
Ratings:
▌ Protocol Coverage ★★★★★ ▌ Legal Defensibility ★★★★☆ ▌ Usability ★★★★
4.6/5.0 – First choice for communication forensics