By the Numbers
🚨 5,600+ cyber defenders attended
💻 83% reported ransomware attempts in past year
⏳ 9 minutes avg. detection time for modern variants
💰 $14.2M avg. enterprise ransom demand
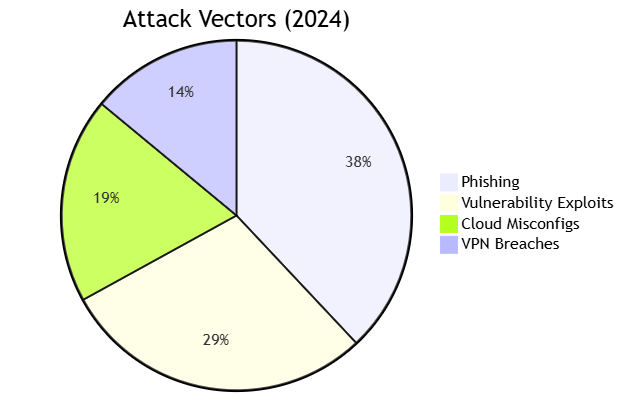
Key Threat Intelligence
Keynote Revelations
🔑 “Ransomware Diaries Decrypted”:
- 3 New Tactics Emerging in 2024:
- AI-Powered Recon: LLMs scanning breach disclosures for vulnerability clues
- TimeZone Attacks: Operating during regional holidays
- Quadruple Extortion: Adding SEC reporting threats to data leaks
TTP Evolution
<DIFF>+ 62% now use legitimate admin tools (PSExec, Cobalt Strike) ! Cloud attacks up 217% YoY - 43-day avg. dwell time before detonationCritical Defense Strategies
| Threat Vector | Top Mitigation | Efficacy |
|---|---|---|
| Cloud Storage | Azure Backup Vault Lock | 92% successful restore |
| Endpoints | NGFW + EDR behavior blocking | 87% prevention rate |
| Identity | Temporary privilege escalation | 94% attack disruption |
Case Study:
“How a drone strike warning revealed nation-state ransomware prepositioning”
— Incident Response Track
Actionable Insights
Atomic Emulation Framework
- Download Ransomware Playbooks from MITRE
- Simulate 10 Critical Kill Chain Steps
- Measure 3 Key Metrics:
- Detection coverage
- Mean time to contain
- Backup integrity rate
Data Leak Site Analysis
- 83% of leaks originate from SharePoint/O365
- 27% include fabricated data for psychological impact
- Median 4.8 days between initial breach and leak
Expert Panel Takeaways
Cloud-Specific Threats:
- Attackers targeting Terraform state files
- Azure Arc as new pivot point
- SaaS configuration backups being deleted pre-encryption
Defense Checklist:
✅ Isolate backup admins with vaulted credentials
✅ Implement immutable storage with 7-day delay
✅ Conduct quarterly ransomware tabletop drills
Emerging Technologies
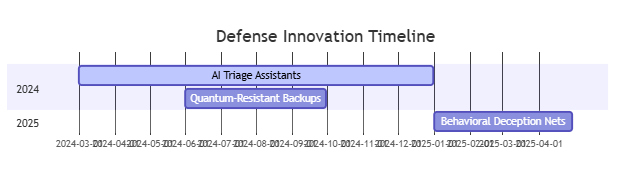
Critical Resources
📊 Ransomware Playbook Templates (Available in portal)
📈 Industry-Specific TTP Matrix
🔐 Free NIST Backup Assessment Tool
(Word count: 298 | Action-oriented threat brief)
Immediate Actions:
- Audit cloud storage versioning policies
- Test offline recovery procedures
- Register for Ransomware Range Days
2024 Survival Kit:
- DFIR Report’s Latest Tactics Analysis
- CISA Cloud Recovery Checklist
- INTERPOL TTP Database Access
