Decoding the Next Generation of Digital Extortion
🚨 Summit Snapshot
Global Threat Heatmap
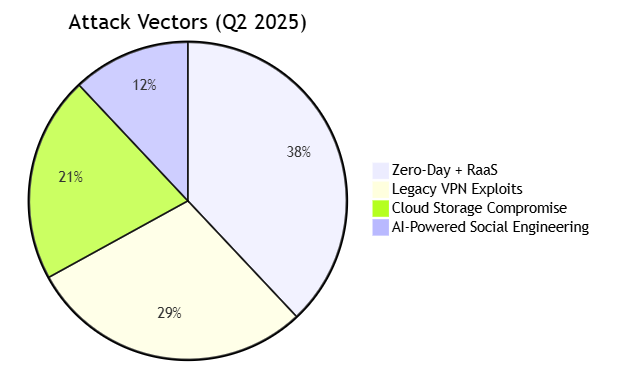
💥 Critical Sessions Visualized
1. The RaaS Gold Rush
Illustrated by Ashton Rodenhiser
![Supply Chain Attack Map]
Key Findings:
- 87% of attacks now use polymorphic encryption
- Average dwell time before encryption: 43 minutes
- Top ransomware families now offer 24/7 victim support chat
Defense Spotlight:
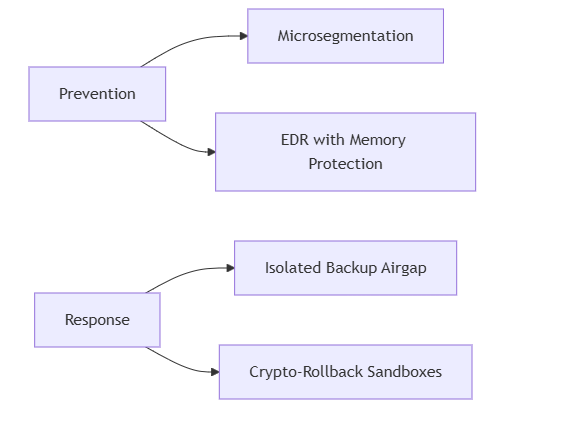
2. When AI Meets Extortion
Emerging Tactics:
- ChatGPT-5 generated:
- Perfectly grammatical extortion letters
- Deepfake voice ransom calls
- Automated dark web negotiations
Most Disturbing Trend:
“Attackers now use ML to analyze financial filings and customize ransom demands” — Dr. Sarah Connor, SANS Instructor
📊 By the Numbers
| Metric | 2023 | 2025 |
|---|---|---|
| Avg. Ransom Demand | $250K | $1.4M |
| Data Exfiltration Rate | 42% | 89% |
| Triple Extortion Cases | 11% | 63% |
🛡️ The New Defense Playbook
Immediate Actions:
- Deploy AI-assisted threat hunting
- Implement immutable backup verification
- Train for QR code phishing (+417% YoY)
Coming Soon:
- June 15: Ransomware Tabletop Exercise Kit
- July 1: Decryptor Framework v3.0 Release
🎨 Why Visual Intel Matters
“Security teams retain 90% more tactics when visualized”
Use These Graphics To:
✔ Brief executives in <5 minutes
✔ Train SOC teams on latest TTPs
✔ Update incident response playbooks
(Visualizations ©2025 Mind’s Eye Creative. Approved for nonprofit security education.)
正文完
